How to Protect Your Network

Ciaran Rooney
20 years: technology, cybersecurity & operations
Hacking isn’t always about a hooded figure furiously tapping away at a keyboard to crack a network’s defences. Sometimes it’s about using a fish tank thermometer in a particularly ingenious way. Join Ciaran Rooney as he explains how we can protect our networks.
Hacking isn’t always about a hooded figure furiously tapping away at a keyboard to crack a network’s defences. Sometimes it’s about using a fish tank thermometer in a particularly ingenious way. Join Ciaran Rooney as he explains how we can protect our networks.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.

How to Protect Your Network
9 mins 22 secs
Security is built in layers, with each layer providing additional protection. There are three layers making up network security. Physical controls (to prevent unauthorised personnel from gaining physical access to network components), technical controls (to protect the data stored on the network once it leaves the application layer) and administrative controls (a set of controls, security policies, and processes that observe and control user behaviour in a network). To protect your network you should implement these controls: use authentication, firewalls, virtual private networks, antivirus software, and network segmentation. Then educate your team and check your settings.
Key learning objectives:
Outline network security controls
Understand the steps to protect your network
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.
What are the three layers of network security controls?
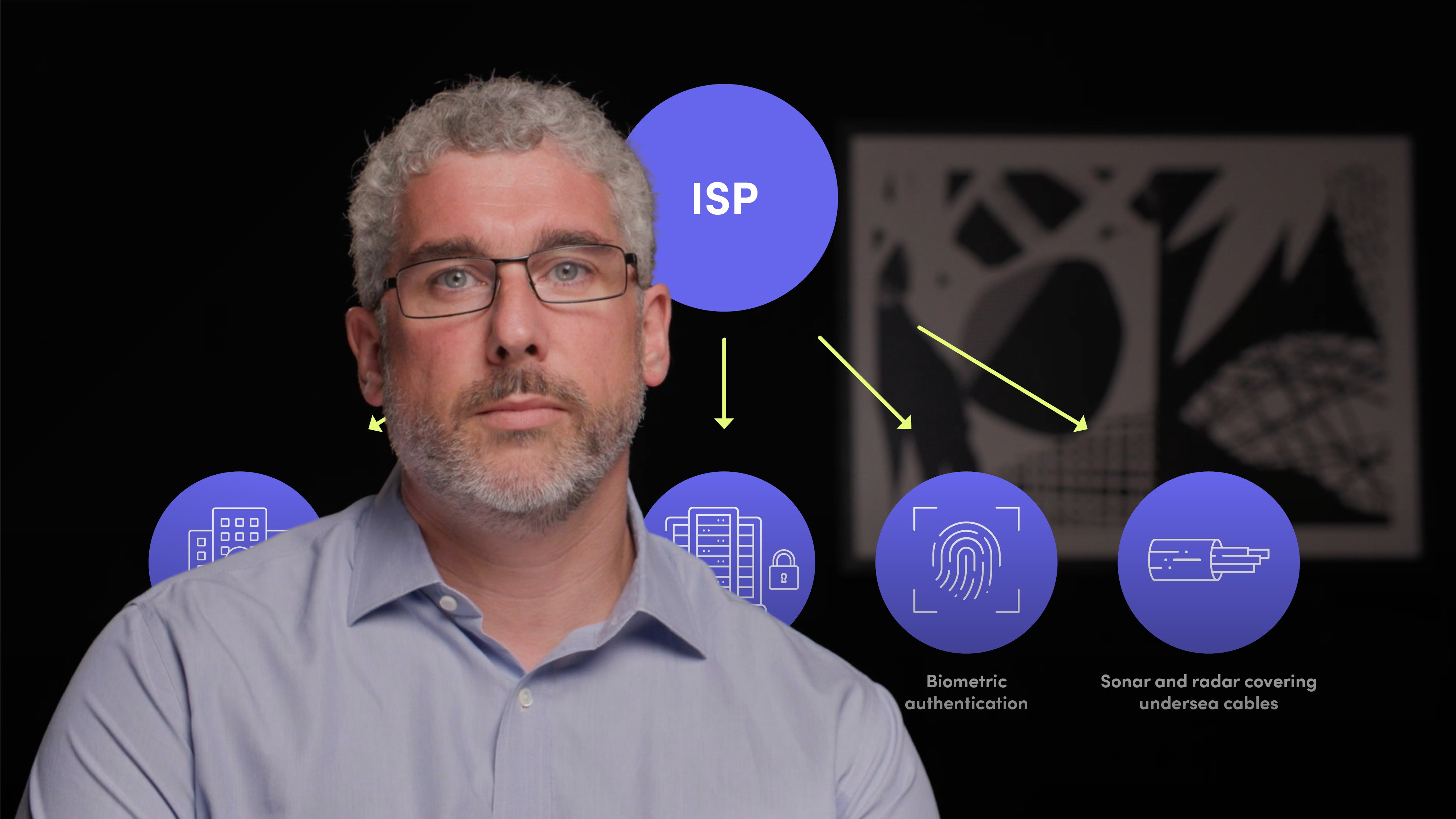
Physical controls: These are in place to prevent unauthorised personnel from gaining physical access to network components such as routers, cables, switches and other network equipment. In companies, physical security is typically locks used to secure their computers, server rooms and LAN equipment. The measures used at ISPs generally are much higher, including; restricted building access controls, CCTV, locked cages in data centres, biometric authentication and sonar and radar covering undersea cables.
Technical controls: These protect the data stored on the network once it leaves the application layer and communicates with our system through to the network layer. They cover the data flowing in and out of the network and implementation is through encryption.
Administrative controls: These are targeted at end-users. They are a set of controls, security policies, and processes that observe and control user behaviour in a network. They contain how different users are recognised in the network, how they are authenticated, what data they can and cannot access and how IT staff can implement changes to the network.
What steps can we take to protect our network?
Authentication: Authentication is a means of verifying your users and is the cornerstone of any security controls. Most businesses and ISPs will now also use two-factor authentication, for further proof of identity, for any employees with access to modify the network.
Firewalls: Firewalls serve as a barrier between untrusted external networks and your trusted network. Network administrators configure rules to analyse and then block or permit traffic onto the network at a packet level. Modern firewalls can be either physical devices or cloud-based web services.
Virtual private networks: A VPN allows you to create a private network connection in software while on a public or unsecured network. All your traffic is routed through the VPN’s secure ‘tunnel’ to a remote server, which is encrypted at a packet level, masking your identity and keeping the data safe whilst in transit.
Antivirus and antimalware software: Good network security should always include installing appropriate antivirus and antimalware software. A good choice is one that constantly scans files in the network and checks files upon entry. These will protect an organisation from a range of malicious software, including viruses, ransomware, worms and trojans.
Network segmentation and access control: Segmentation is the practice of splitting your network by access level and purpose. This is one of the essential security measures organisations and individuals can undertake. It helps in safeguarding both users and devices from hackers on the internet, as even if one device on the network is compromised, it prevents it from accessing all parts of your network.
Education: Keeping people educated on what to do and what not to do is incredibly important. Attackers can send a phishing email to thousands of people, but it only requires one person to make an error that can bring down an entire network. Ensuring that people report all suspected threats, as standard, means that you will be better prepared and can reduce the possible harm caused or even prevent it altogether if a mistake is made.
Check your settings: When it comes to all of your network devices, make sure that you always check the settings and avoid using the default username, password or other insecure settings provided when you first bought the device. Ensure you understand all the features your device offers and disable any that you don’t need, or that could potentially threaten your network.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.

Ciaran Rooney
There are no available videos from "Ciaran Rooney"