Blockchain Security

Igor Pejic
Financial technology & blockchain specialist
The blockchain is often hailed for its immaculate security, its immutability, and the protection of its users’ identities. To uncover the true level of security, Igor discusses the mechanism itself, transaction validation and other criticisms.
The blockchain is often hailed for its immaculate security, its immutability, and the protection of its users’ identities. To uncover the true level of security, Igor discusses the mechanism itself, transaction validation and other criticisms.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.

Blockchain Security
9 mins 42 secs
Key learning objectives:
Explain why nodes would invest resources/computing power into the blockchain network
Understand whether attackers change blockchain history
Understand the 51% attack and why is it unlikely
Overview:
The blockchain is often hailed for its immaculate security, its immutability, and the protection of its users’ identities. However, there have been many cases where exchanges have been hacked and cryptocoins have been stolen. These hacks can be attributed to lax security standards not in the blockchain-system itself, but in the management and storage of data such as private access keys. The blockchain itself has proven extremely resilient and as more transactions are added to the chains of cryptocurrencies such as bitcoin, the safer the mechanism becomes.
Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.
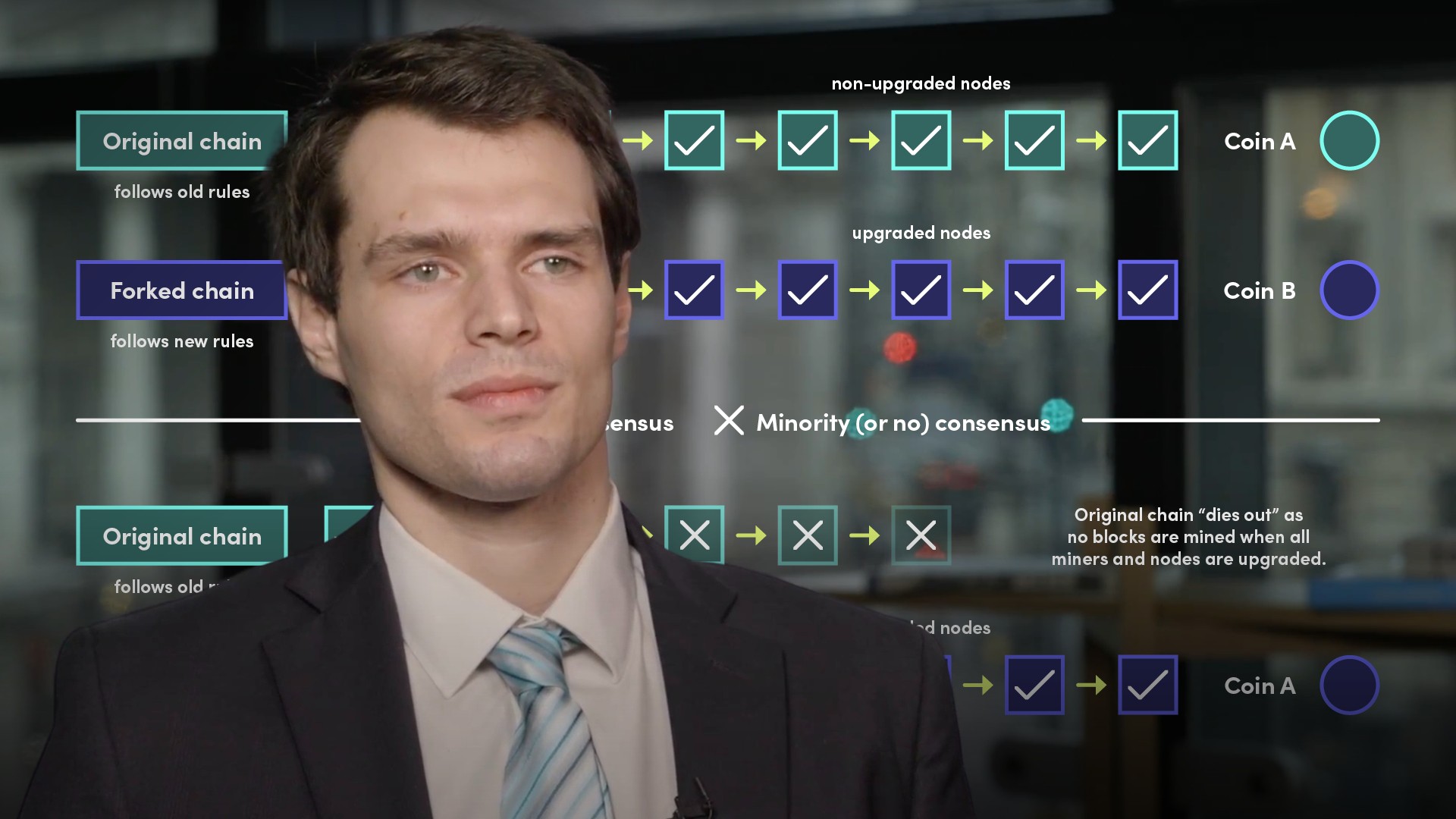
Can attackers change blockchain history?
This answer depends on the validation mechanism each particular blockchain uses. With the so-called proof-of-work validation, each bitcoin transaction is encrypted into a hash value that is unique and has uniform length. This is done via one-way cryptography; so, if someone only has the hash value, they can’t find the initial input variables. The header of a block contains hash values referring to the previous block meaning altering the preceding block becomes impossible without alerting all subsequent blocks. This makes the chain tamper-proof.Explain why nodes would invest resources/computing power into the blockchain network
Validator nodes, also known as miners, invest massive computing power to solve a mathematical puzzle with trial and error mechanisms. The miners decide which transactions to include in each new block and the node that hits the right solution first is rewarded with freshly minted bitcoins.What is a 51% attack and why is it unlikely?
Before the winning node receives the credit for solving the mathematical puzzle, the other miners must verify the proposed solution. The verification can be performed very quickly once the correct value is found, however, if a possible hacker was to gain control of over 50% of the hashing power in a network, they could vote a ‘wrong’ truth into reality. This scenario is known as the 51% attack and it poses a threat to future transaction validity. However, the attack is extremely unlikely due to the sheer computing power required to control over 50% of the network, but considering that miners are joining in mining pools, it is not completely impossible to manipulate future transactions.Subscribe to watch
Access this and all of the content on our platform by signing up for a 7-day free trial.

Igor Pejic
There are no available Videos from "Igor Pejic"